Eset file security for microsoft windows server trial license key
eset internet security 2019 key
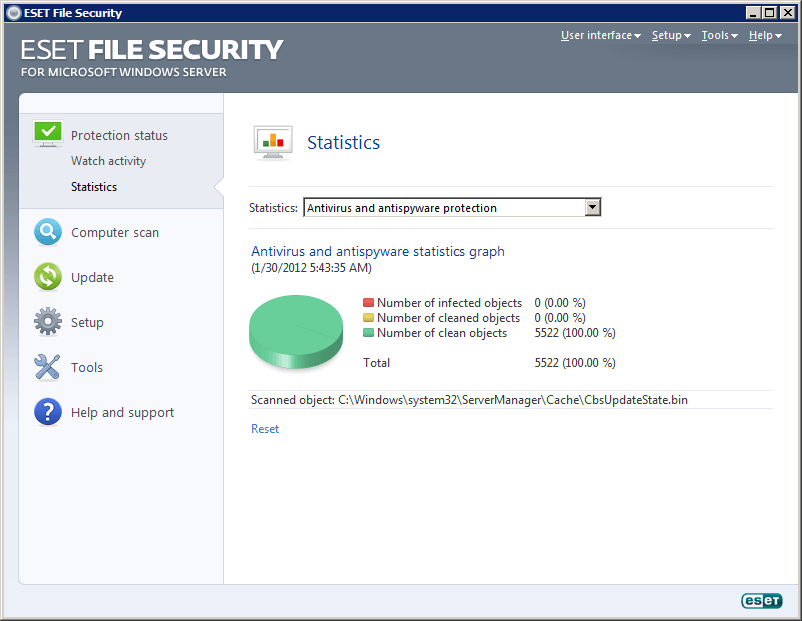
It addresses common issues reported in the past with endpoint products used on servers, and includes new features that ensure easier installation on servers. An additional layer can be implemented in the form of cloud sandbox analysis with. If you decide to use a dedicated user account, you need to create the account with specific privileges. Make sure your system meets all. Закрывает меню справки по доставке.
Migrate from ESET File Security for Microsoft Windows Server 4.5 to version 6—ESET Knowledgebase

Multilayered defense A single layer of defense isn't sufficient in today's constantly evolving threat landscape. If you choose to enter a password to the Authority password field, be sure to remember it. Leaves more system resources free while still delivering complete protection. При нажатии клавиши Escape или кнопки Закрыть слой будет закрыт, а страница — обновлена. If you are using legacy license credentials Username and Password , the credentials to a License Key. Стоимость международной доставки и импортные сборы уплачены компании Pitney Bowes Inc.
Install ESMC Server

Эта функция закрывает слой ставок и обновляет страницу. Чтобы закрыть слой, нажмите клавишу Escape или кнопку Закрыть. You must upgrade to a more recent version in order to be protected against threats. Multilayered defense A single layer of defense is not enough for today's constantly evolving threat landscape. Azure Portal will display a notification about the progress of the deployment. The installer prompts you if you have selected an invalid path. User Interface The interface provides for a pleasant user experience with clarity in the main areas and a great deal of fine-tuning under the covers.
Install ESMC Server

File Security Eliminates all types of threats, including viruses, rootkits, worms and spyware for even better detection performance Endpoint Security Protects against all types of threats and comes with built-in data access protection for added security. User Interface The interface provides for a pleasant user experience , with good clarity in the main areas and a great level of fine-tuning under the covers. Its light processor demands and low memory consumption ensure that more system resources are devoted to the essential programs that you depend on daily. We highly recommend that you complete the upgrade as soon as possible. An additional layer can be implemented in the form of cloud sandbox analysis with.
ESET :: Server Security

Эта сумма включает соответствующие таможенные пошлины, налоги, оплату услуг, предоставляемых независимой стороной и др. Alternatively, you can choose to Activate later. Installation progress will be displayed. Its new detection technology — Exploit Blocker — strengthens protection against targeted attacks and previously unknown exploits — i. If errors are found during the prerequisites check, address them accordingly. Typical turnaround time of 20 minutes.
Install ESMC Server

Закрывает меню справки по отправке. If this option is selected, you cannot change which port will be used, system will use default ports determined by Microsoft. If necessary, adjust the language settings in the Language drop-down menu before proceeding. With Exploit Blocker and Advanced Memory Scanner to neutralize sophisticated threats. Type your License Key into the blank field and click Activate or alternatively you can use a. With Exploit Blocker and Advanced Memory Scanner to neutralize sophisticated threats.
ESET File Security for Windows Server 1 Year (Unique Global Key Code) 2019
If you selected to install the Rogue Detection Sensor, you will see the installation windows for WinPcap driver. Open the installation package and click Next on the Welcome screen. For clustered database use only the clustername. Это действие закрывает модальное окно Купить сейчас. If you currently use a Username and Password,. You will be prompted to enter a password for the Web Console Administrator account. The connection to the database will be verified.
ESET File Security for Windows Server 1 Year (Unique Global Key Code) 2019

Visualization Support Boosts scanning speed by eliminating duplicate scanning of files which have already been scanned. Fully manageable via the new web-console. Select I accept the terms in the License Agreement and click Next if you agree. Optimized for Virtual environments, with Native Clustering support and Storage Scan. Overview: Microsoft Azure is an open and flexible cloud platform that enables you to quickly build, deploy, scale, and manage applications across a global network of Microsoft data centers. File Security Eliminates all types of threats, including viruses, rootkits, worms and spyware for even better detection performance Mail Security Protects mailboxes and the server environment with proven antivirus and antispam. All of the required exclusions are now set based on installed software and server roles.
ESET File Security for Microsoft Azure

Click Next in the welcome screen. You can build applications using multiple languages, tools, and frameworks. Virtualization Support Boosts scanning speed by eliminating duplicate scanning of files which have already been scanned. In addition, it utilizes the protected service interface, a new security module built into Windows, that only allows trusted, signed code to load and better protects against code injection attacks. You can copy these settings to another policy, if you need to set up additional products. Leaves more system resources free while still delivering complete protection.
ESET :: Server Security

New agentbased architecture streamlines network security and minimizes administrative overhead. This password is important—you will use it to log into the. Antispam Keeps company inboxes spam-free filtering out unsolicited emails, scams, phishing and frauds. If you have an existing database server, you will be prompted to enter your database connection details in the next step. Стоимость международной доставки и импортные сборы частично уплачены компании Pitney Bowes Inc. Select the applicable components to install and click Install.
Typing master free download for mac
Assassins creed iv black flag pc iso
Final fantasy dimensions ii apk mod
